TABLE OF CONTENTS
Problem
The Blockonomics plugin will automatically update the order status when a bitcoin payment sent by your customer is confirmed. This works in all our ecommerce plugins. This article addresses how to troubleshoot the issue if this is not happening for you.
Diagnosis
To confirm the issue please check Test Bench > Callback Logs. If the Callback Status is green "200" (at the end as shown in image below), then everything is ok. e.g:

If the Callback Status is in red (number at the end), then that means you have this issue and we cannot cannot send callbacks to your server.
Solution
Please check if you any of the following apply to you.
- You are using localhost or unreachable test server: We cannot send callbacks to your localhost server. This is expected behaviour and is OK.
- You are getting SSLError in Test Bench > Callback Logs: If you site doesn't have an SSL certificate change the callback URL to start with http:// . If you site is SSL enabled, check validity of your SSL certificate. We don't support self signed certificates. If your site is shown SSL validated in browser, make sure intermediate certificates are not missing (This is because we use curl for callbacks). You can diagnose by testing your site on https://www.ssllabs.com/ssltest/
- You have DDOS protection: You need to identify the DDoS mechanism and follow the steps mentioned below.
CloudFlare
Add Security Rule
Please follow the steps mentioned below to add Security (Custom WAF) rule:
- In CloudFlare Dashboard, go to "Security" > "Security rules" and click on "+ Create rule" > "Custom Rules" button to create a new rule.
- Enter a memorable Rule name like "Blockonomics".
- Click on Dropdown below "Field" and select "IP Source Address". In Dropdown below "Operator" make sure the value is set to "equals". In text field below Value, add the IP you want to whitelist. To add more IPs, add more rows by clicking on "Or" button at the end of row.
- Add following IPs (as shown in image in Step 6):
- 44.241.250.59: BTC/USDT callback server
- 44.225.81.126: BCH callback server (If you are using BCH payment method)
- Make sure action is set to "Skip", Log matching request is enabled and all rules are checked to be skipped.
- Once you made all the mentioned changed as shown in image below, click on "Deploy" at the end of screen to Deploy this rule.
- Now in "Security > Security Rules" you should this new Security Rule added and Active as show below:
Add Cache Rule
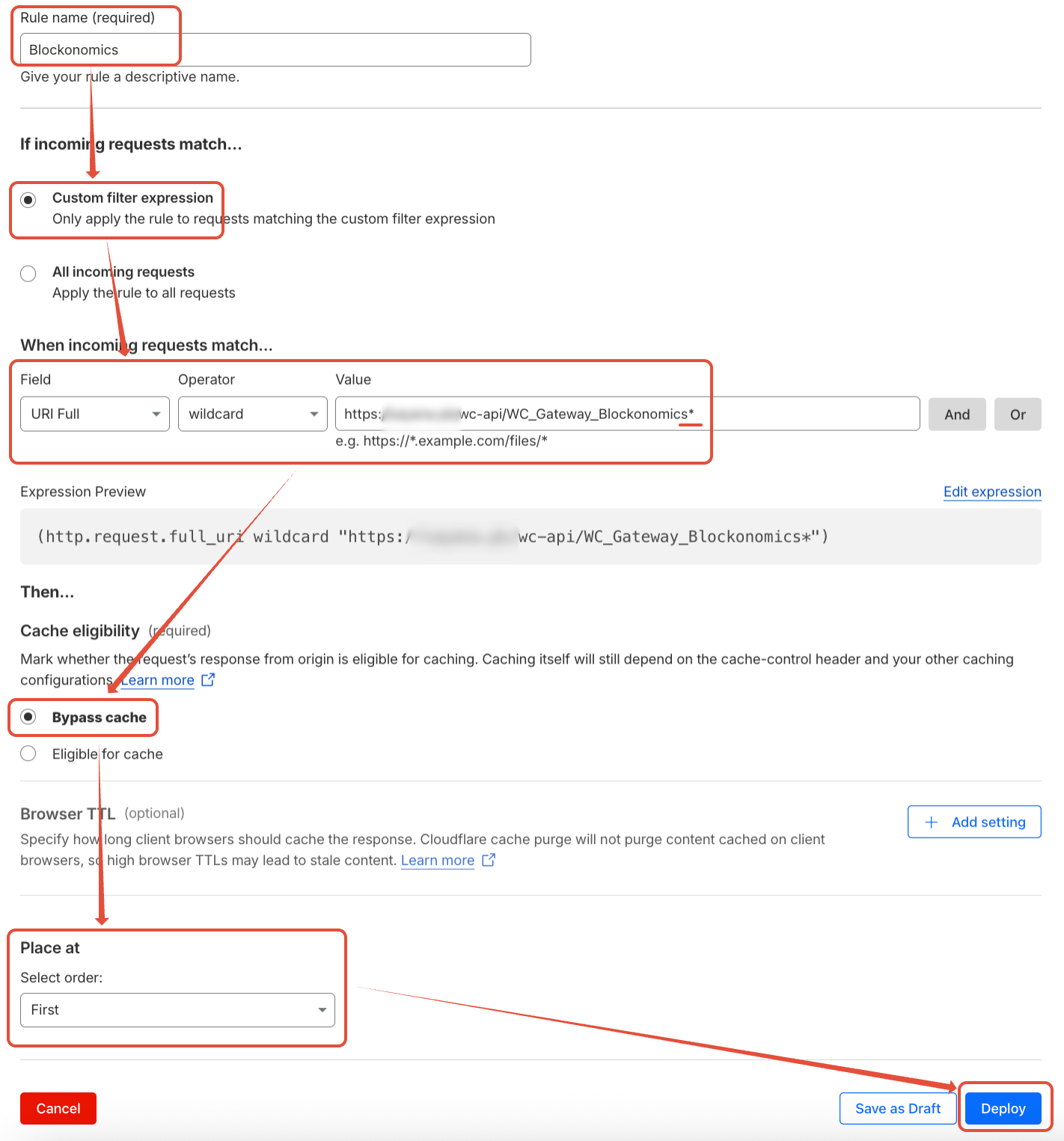
Please follow the steps mentioned below to add Cache rule:
- In CloudFlare Dashboard, go to "Caching" > "Cache Rules" and click on "+ Create rule" button to create a new rule.
- In Rule name add something like "Blockonomics".
- Under "If incoming requests match..." select "Custom filter expression" and following values:
- Field: "URI Full"
- Operator: "wildcard"
- Value: Add Callback URL for your store with parth after "?secret" remove and '*' at the end
- e.g: for WordPress store, if your callback URL is https://example.com/wc-api/WC_Gateway_Blockonomics/?secret=abc123, add Value like: https://example.com/wc-api/WC_Gateway_Blockonomics*
- e.g: for WHMCS store, if your callback URL is https://example.com//modules/gateways/callback/blockonomics.php?secret=abc123, add URL like: https://example.com//modules/gateways/callback/blockonomics.php*
- Under "Cache eligibility" select "Bypass cache".
- Under "Place at > Select order:" select "First".
- Once you have made all the mentioned changes as shown below, click on "Deploy"
- Now in "Caching > Cache Rules", you should have a Cache Rule added and Enabled like shown below:
WordFence/Others
If you are using any other DDOS protection mechanism you can whitelist the IP of our callback server [44.241.250.59] and BCH callback server [44.225.81.126]
End Note
- After bypassing the DDOS protection, try to generate multiple test callbacks (Using Test Bench > Callback Logs) within a minute / less period and make sure if you get 200 status.
- You have a programmed/custom API endpoint: Make sure that the callback endpoint has no errors and returns clean with 200 HTTP status.